A group of hackers successfully accessed a Bitcoin wallet that had remained locked for 11 years and have now revealed how they managed to break into it.
It’s a common and frustrating situation: knowing you have funds, yet being unable to use them.
Think of when you’re awaiting your paycheck to hit your account so you can indulge in that pumpkin spice latte you’ve been eyeing.

Many can relate to this scenario, but now imagine the stakes if your expected amount was $3 million, and you had to unlock it with a forgotten password instead of just waiting for a bank deposit.
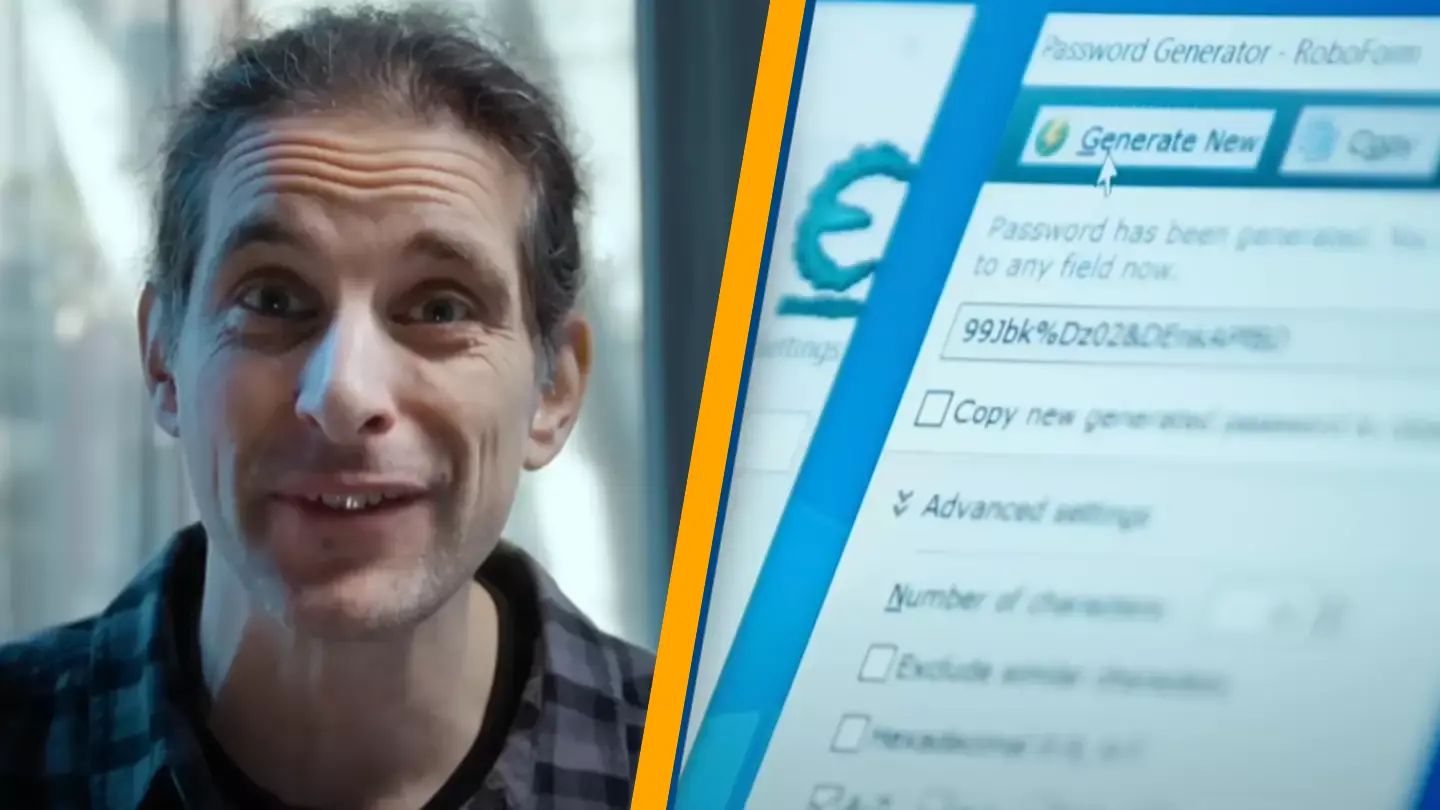
This was the predicament faced by a crypto holder who forgot the password to his Bitcoin wallet, generated by a program called Roboform.
In a YouTube video by electrical engineer Joe Grand, the wallet’s owner shared: “I generated the password, I copied it, put it in the passphrase of the wallet, and also in a text file that I then encrypted.”

At the time of forgetting the password, the Bitcoin was valued at a few thousand dollars, but as its worth surged by over 20,000 percent, he found himself locked out of $3 million.
The owner confessed to Wired he was ‘really paranoid’ about his security, but fortunately, help came from Grand, who is known as ‘Kingpin’ in online circles.
Grand gained recognition in the crypto world in 2022 when he assisted another crypto user in retrieving access to more than $2 million in digital currency thought to be lost permanently.
Luckily, Grand was once again ready to assist this crypto owner and has detailed his process.
In his YouTube demonstration, Grand illustrated that he used a tool by the US National Security Agency (NSA) to break down the password generator’s code.
https://www.youtube.com/watch?v=o5IySpAkThg
“In a perfect world, when you generate a password with a password generator, you expect to get a unique, random output each time that no one else has,” he detailed.
“[But] in this version of RoboForm, it was not the case. While RoboForm’s passwords appear to be randomly generated, they’re not. With the older versions of this software, if we can control the time, we can control the password.”
By manipulating the system, Grand set the time back to when the password was originally generated.
Working together with his colleague Bruno, they managed to decipher the code.
However, despite their understanding of the system, Grand acknowledged they were fortunate.
He told Wired via email: “We ultimately got lucky that our parameters and time range was right. If either of those were wrong, we would have … continued to take guesses/shots in the dark.”